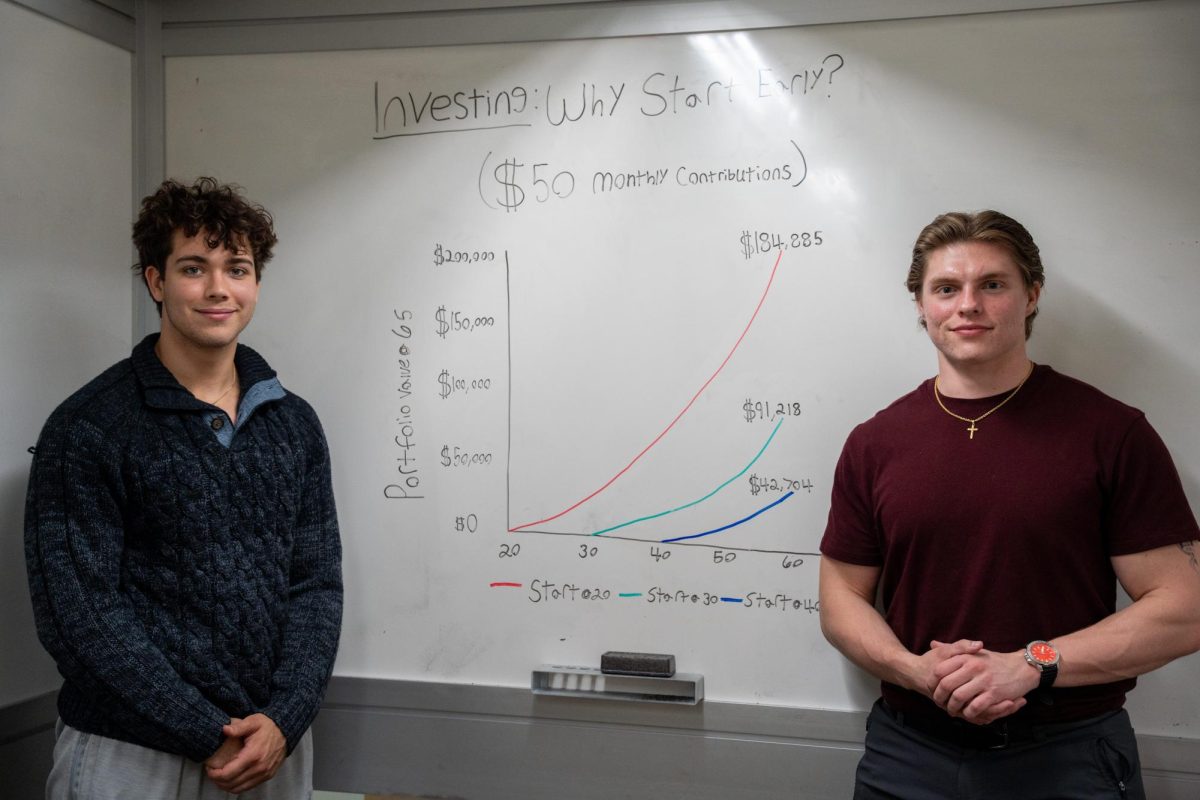
By Eva Hill
hilleva@grinnell.edu
The Grinnell College Cyber Risk Governance Committee (CRGC) has released its proposed new technological security rules for College employees who have access to sensitive personal data, less than a year after last spring’s incidents of compromised student Social Security numbers. The protocol, named the Written Information Security Program (WISP), would require employees with access to private information to strengthen the security practices they use on their Internet-connected devices. Students, faculty and staff of the College will be able to submit anonymous comments on the WISP until March 13 via a link provided in the email announcing the program.
Two employees of Information and Technology Services (ITS) gave more detail on the WISP to The S&B via email (according to ITS Communications Manager Missy Gansen, it is ITS policy for employees to give only email interviews to the media).
ITS Chief Information Officer Dan Robinson wrote, “Our increased security results from several aspects of the WISP: awareness and education around the threats that exist; the practical steps that we can all take to safeguard data; and the technical controlsthat should be in place to minimize the risks of data exposure.”
The information that the WISP is specifically intended to safeguard is “data that should be protected to secure an individual’s privacy (protection against identity theft) and information that could be used to benefit a potential bad actor financially, such as credit card details (protection against fraud),” Robinson wrote.
Identity privacy remains a major issue in online scams and security breaches today; last year, students who had applied to Grinnell received an email offering them the ability to view their applicant file in exchange for a fee prior to the official decisions being released by the college.
First-years Kendra Howard and Amna Kapur both recalled receiving the email with the offer to view their file before Grinnell’s decision date. “It’s definitely concerning,” said Howard. Kapur added, “Obviously, they [the person who accessed the files] would have had access to all our information, and that’s really sensitive information.” Most students will be relatively unaffected by the WISP, which includes rules on securing Internet-connected devices at work and during travel, as well as protocols for security levels and encryption on those devices.
However, Robinson noted that the training program provided in the WISP “will be made available to all students.” For College employees whose jobs do qualify for the WISP, including the small number of students with access to other students’ sensitive personal information, their work already includes security guidelines of the kind outlined in the WISP, according to ITS Deputy Chief Information Officer Jonathan Colby.
Colby wrote, “As the stewards of the College’s Information Security program, the CRGC recognized the importance of widely distributing information about the safeguards and ensuring that the program was reviewed regularly.”
On the comment period, Colby wrote, “While the committee will not be able to change anything that is legally required to be present in the WISP, they are interested in any improvements that we anticipate will be identified by employees and students alike.”
Asked what she thought of the proposed protocols, Kapur said, “That makes sense – that sounds like a positive thing.”